Identity & Access Management (IAM)
A new standard for secure access and lifecycle management
Secure Remote Work.
Streamline Hypergrowth.
2020 has introduced the concept of predominantly-remote work to almost every office-based business around the globe. These employees mostly use their public or home internet connection to access the company’s business applications – which presents an increased risk of account takeovers by cybercriminals, and other insider threats. Therefore, no security stack – or Zero Trust strategy – can go without authenticating employee interactions with business applications anytime, from anywhere.
The obvious basics of IAM are SSO and adaptive MFA, to enforce authentication with minimum friction throughout the workday. But today’s IAM goes way beyond that, with passwordless authentication and automated provisioning throughout the employee’s entire lifecycle. This means large-scale recruitments with no hassle to IT or HR teams, and effortlessly mainaining least-privilege upon offboarding and role changes.
Download
Watch
How IAM Amplifies Security & Business

Wide Integration Catalogue
Wide Integration Catalogue

Next-Gen MFA & SSO
Next-Gen MFA & SSO
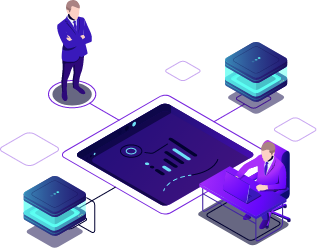
Employee Lifecycle Automation
Employee Lifecycle Automation

Compliance
Compliance
Implementing IAM with GlobalDots
-
Integration Experts
Leverage our experience to integrate every single application and completely eliminate in-app sign on. Receive custom integrations, including undocumented ones which require API work, or more common platforms like Gsuite, Office365, and HR systems.
-
Compliance Enablers
Get an expert’s touch in policy configurations, weaving all relevant best practices into your employees’ daily operations. Peacefully head on to mergers and funding, ensuring compliance with common standards like ISO 27001, SOC2, etc.
-
Smooth Onboarding
Launching or replacing an IAM solution can be stressful. Everything has to function flawlessly, otherwise angry emails will start pouring in. As most vendors have only basic support centers, having an expert partner to walk you through can shorten adoption time by 50%.
-
Certified Partners
s part of the Okta Ozone community, we always know what's coming up. Communicating directly with vendor product teams, we are able to influence their roadmaps based on our customers’ needs.
Challenges Answered
Controlling User Access
Controlling who has access to which applications becomes a real challenge when users can get access from any browser, from any place, at any time As Cloud apps have inגdependent user stores that are not integrated with on-premises directories, users have to remember more passwords, and IT has to manage multiple accounts and map users between directories and cloud applications. This is typically a manual process, and it can get messy fast. This situation is exacerbated with the cloud as IT is often not involved in the purchasing process. GlobalDots introduces IAM solutions that let IT take back control, while simultaneously adding a critical layer of security and ease of use. It creates a directory-based employee system of record so IT can easily view and manage user data.
Password Fatigue
Visit any organization that has adopted a reasonable number of cloud apps and you will find people suffering from password fatigue. Not only must users remember a constantly changing set of passwords, but each cloud app has different password requirements. To lessen the burden, people resort to obvious passwords, sticky notes, and spreadsheets. They all but issue an invitation to an outsider seeking to breach the network. Luckily, password fatigue has an easy cure: Single Sign-On (SSO) lets users access any app with a single set of credentials. Passwordless authentication means this set is constantly and automatically changing, with absolutely no hassle to the user.
Collaborative Administration
Each cloud application has a unique administration model. This can create friction between the business, which needs to customize and manage the app to respond to changing needs, and IT, which is responsible for identity and access management across the entire organization. We solve this problem by letting IT manage users, apps and devices from a single, integrated platform. Meanwhile, the business gets the control they need.
Managing ROI and Compliance
To calculate the ROI of cloud apps, IT must understand how the apps are actually being used, against paid-for capacities. In addition, depending on the industry and circumstance, IT must constantly monitor and control which users have access to certain cloud applications in order to comply with governmental regulations. GlobalDots introduces IAM solutions that make usage tracking easy, and also puts apps and data behind a compliance wall.
Keep Exploring on the GlobalDots Blog
From Our Experts
How-To: Automated NS1 Provisioning with Okta Workflows
While Okta and NS1 support SAML Authentication, Provisioning and de-provisioning users still requires manual work.
From Our Experts
Automated Workflows – IT & HR Dreams Come True
At times when interest rates are close to zero and VC money flows into startups and tech companies, we see a spike in...
From Our Experts
The Future is Passwordless: 3 Reasons You Need a Passwordless Solution Now
Passwordless authentication is the key to simplifying and streamlining the process of connecting employees to all systems company-wide.
From Our Experts
How-To Guide: Okta and Akamai Integration
Read this step-by-step guide and learn how to integrate Okta and Akamai.
About GlobalDots
GlobalDots is a 17-year world leader in cloud innovation, connecting businesses with the latest cloud & web technologies.
Fusing an insatiable hunger for innovation with a diligent team of hands-on experts, we help our customers maintain an up-to-date technology position in a quickly-changing world.
We consult, resell, implement, and customize full-stack solutions, including cost & performance optimization, security, connectivity, and managed services, to streamline business processes and provide the foundation for sustainable business growth.
Trusted By




























Talk to an Expert &
Request a Demo
Schedule a call with our experts. Discover new technology to improve your performance, and get web security recommendations.
Innovation challenged customized put to work supported
Innovation Challenged
Our engineers explore & evaluate multiple vendors for each new technology, only introducing to our portfolio what meets their uncompromising standards and thorough examination.
Innovation Customized
We are young cloud industry veterans, intimate with the ins-and-outs of every technology we deal with. We deliver a fully integrated and configured solution, even when custom developments are required.
Innovation Put To Work
With our expertise, rest assured you utilize the full arc of features and capabilities, to optimize your performance and protection in a cost-effective manner.
Innovation Supported
We proactively advise newer, better solutions, to keep one trouble off your plate and allow you focus on your top priority - development and revenue generation.
Follow Us
© 2021 GlobalDots. All rights reserved.
Here you can find our Privacy Policy and GDPR Privacy Notice | Privacy Settings
This site uses third-party website tracking technologies to provide and continually improve our services, and to display advertisements according to users' interests. I agree and may revoke or change my consent at any time with effect for the future.




